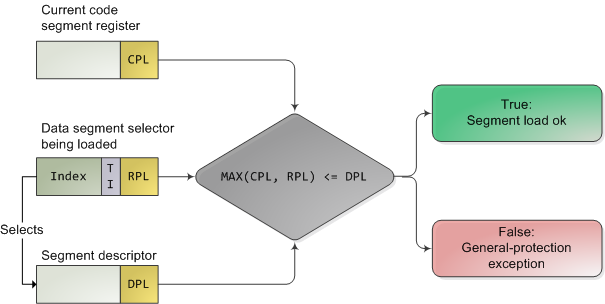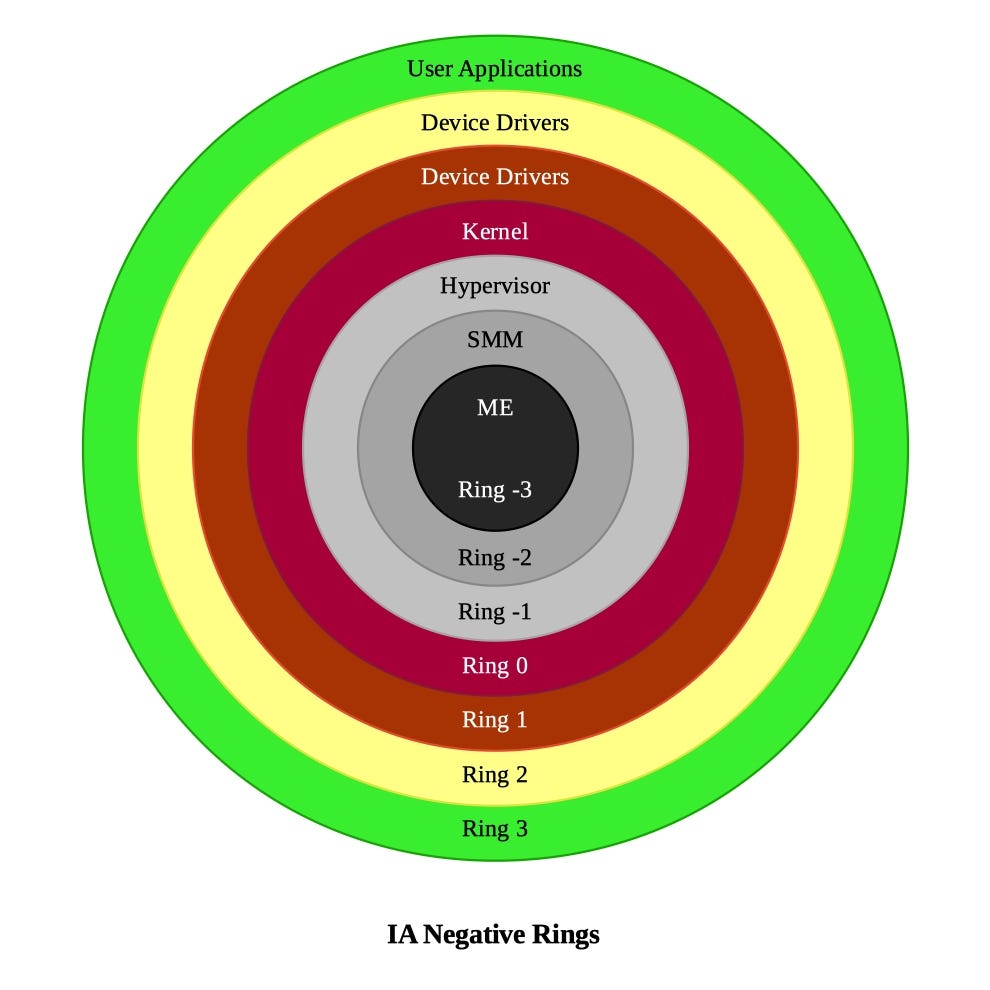
Negative Rings in Intel Architecture: The Security Threats That You've Probably Never Heard Of | by RealWorldCyberSecurity | The Startup | Medium
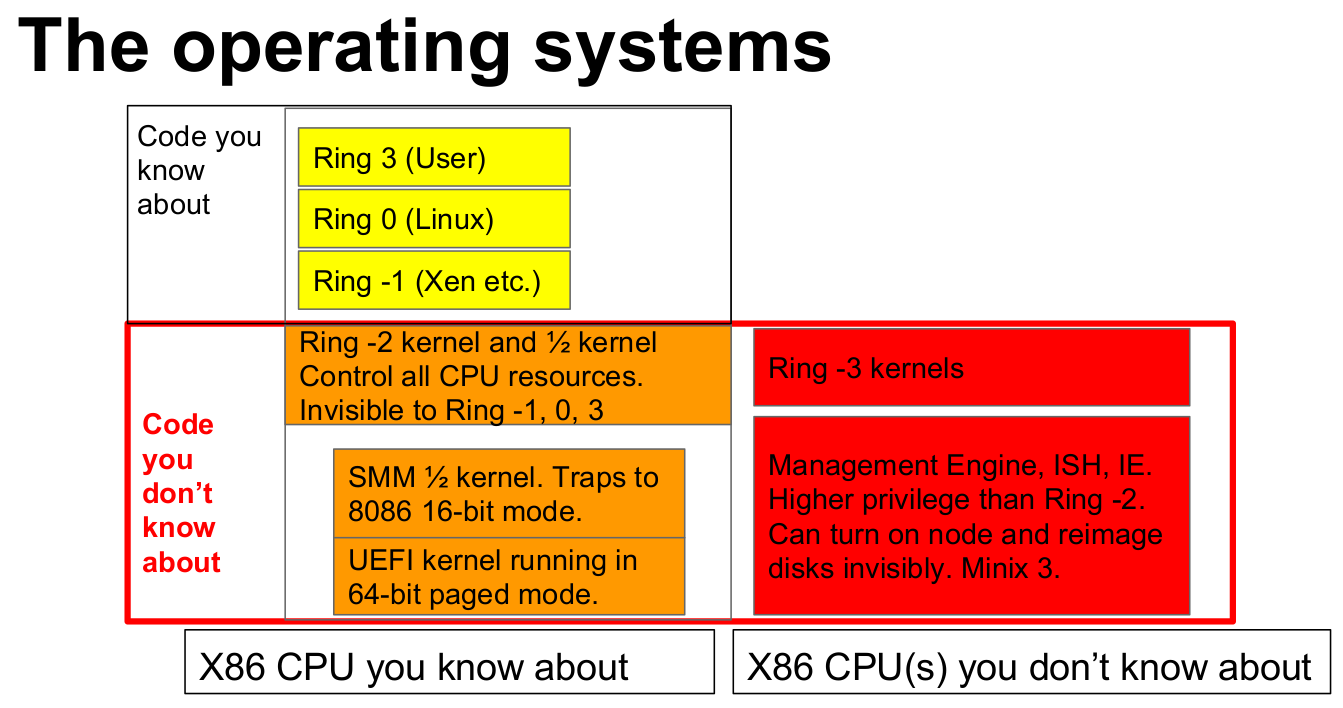
MINIX based Intel Management Engine Firmware & UEFI are Closed Source & Insecure, NERF to the Rescue! - CNX Software

CNIT 127: Exploit Development Ch 3: Shellcode. Topics Protection rings Syscalls Shellcode nasm Assembler ld GNU Linker objdump to see contents of object. - ppt download
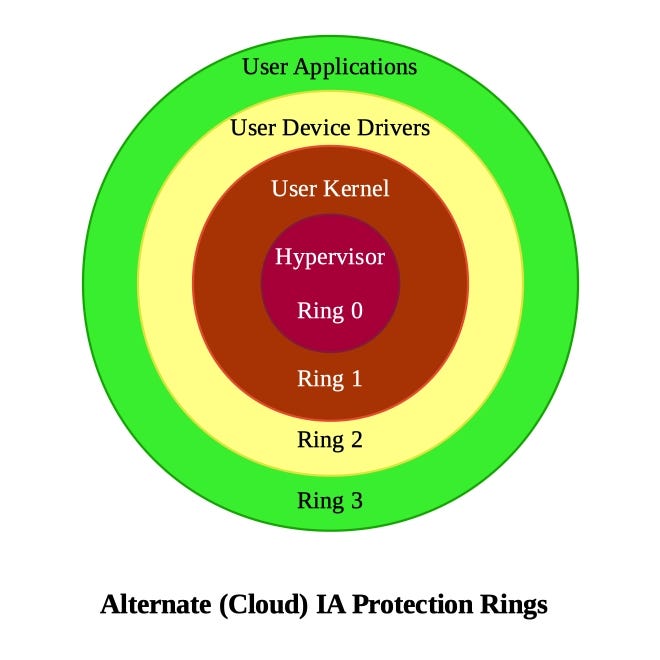



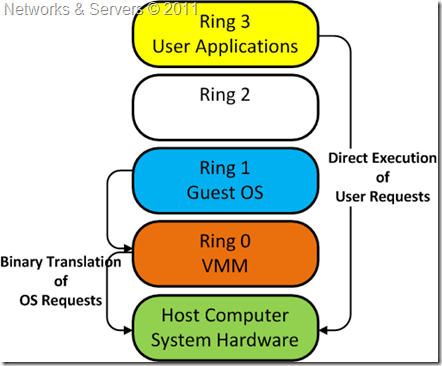

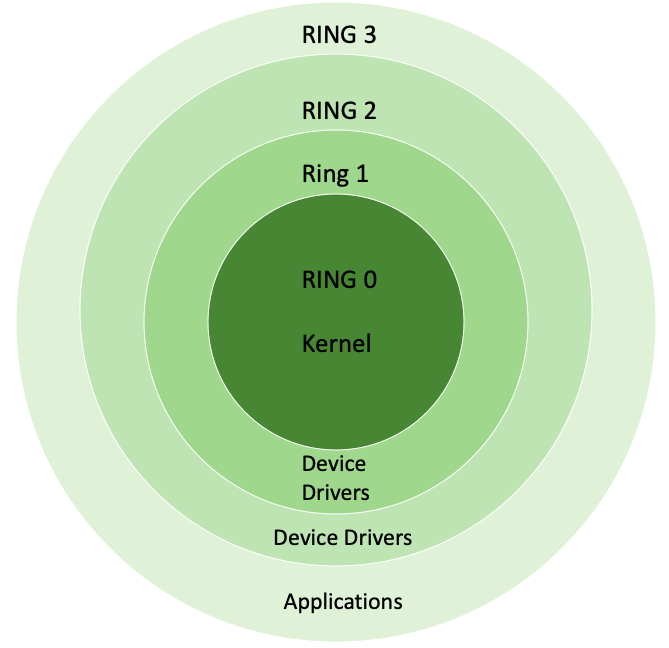
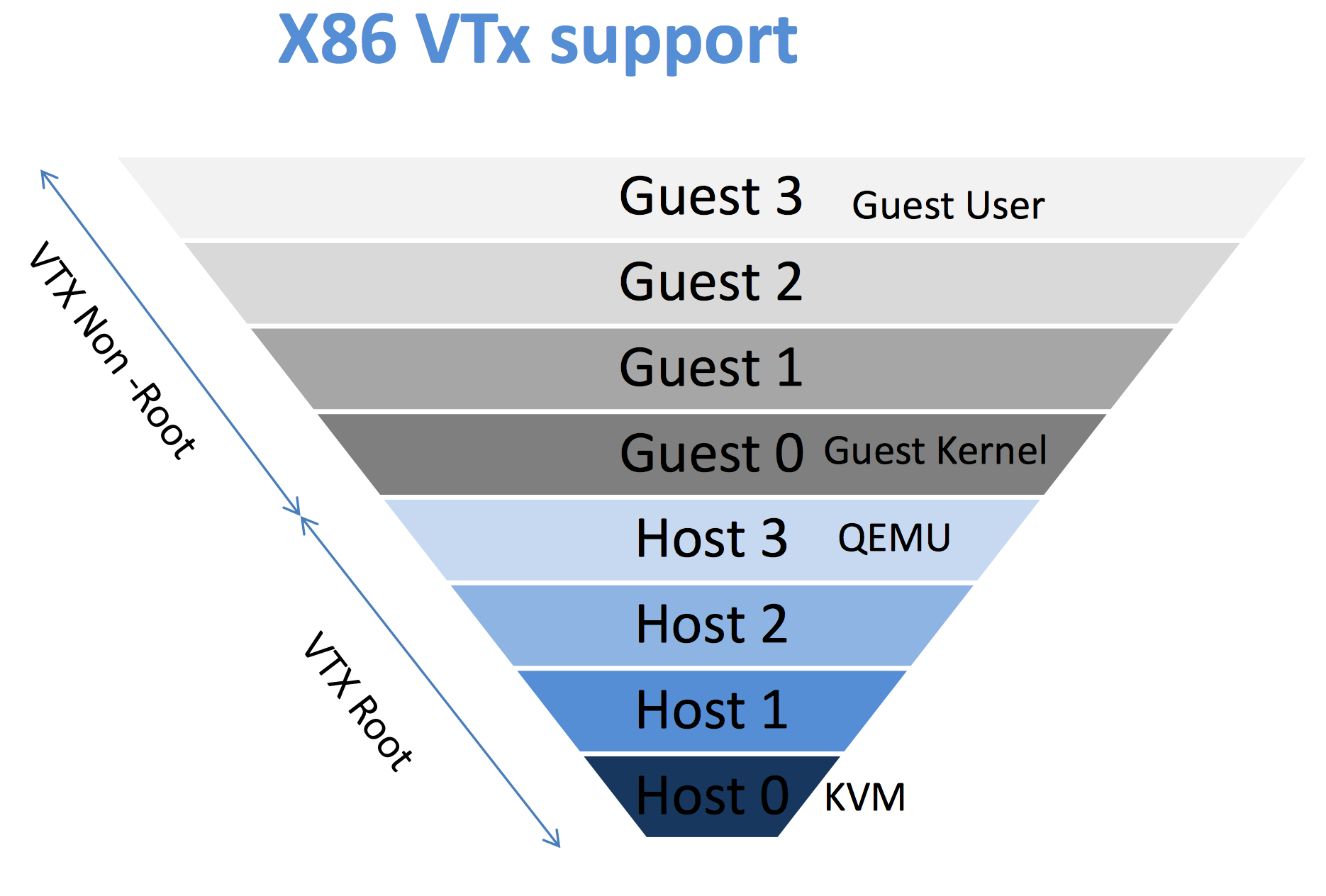
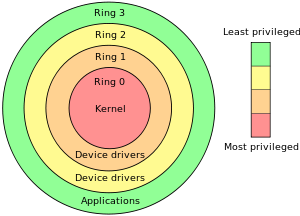



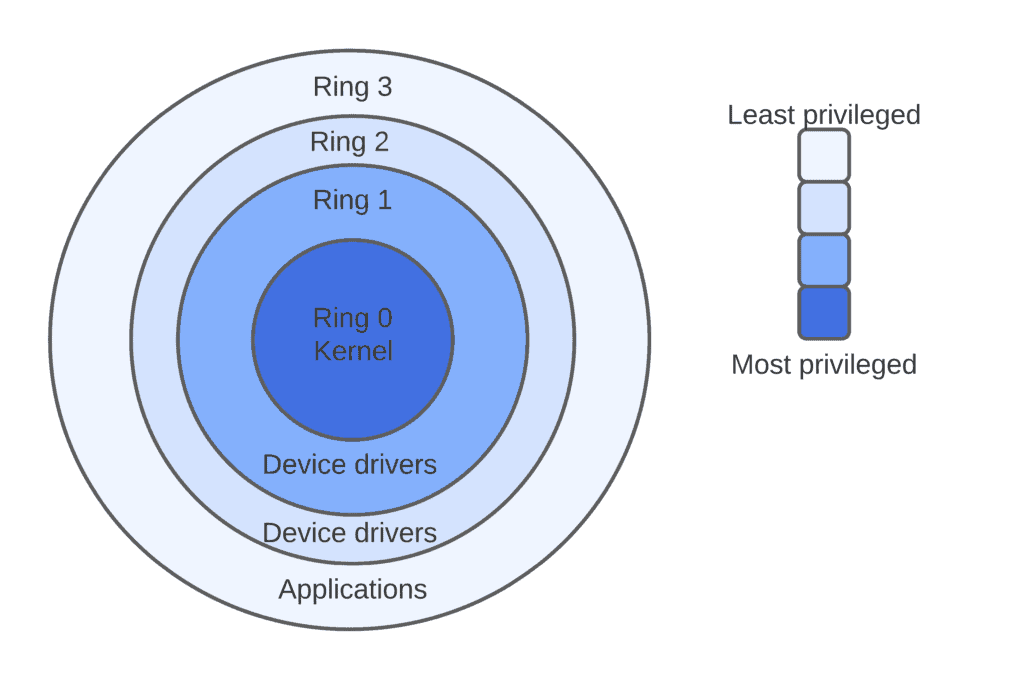

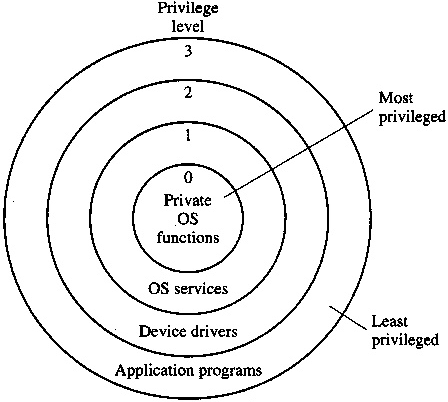
![Execution Rings for the x86 64 Architecture. See also [19] | Download Scientific Diagram Execution Rings for the x86 64 Architecture. See also [19] | Download Scientific Diagram](https://www.researchgate.net/profile/Roberto-Pietro/publication/326696873/figure/fig1/AS:655531282796567@1533302245961/Execution-Rings-for-the-x86-64-Architecture-See-also-19_Q320.jpg)